ThreatSpike Blog
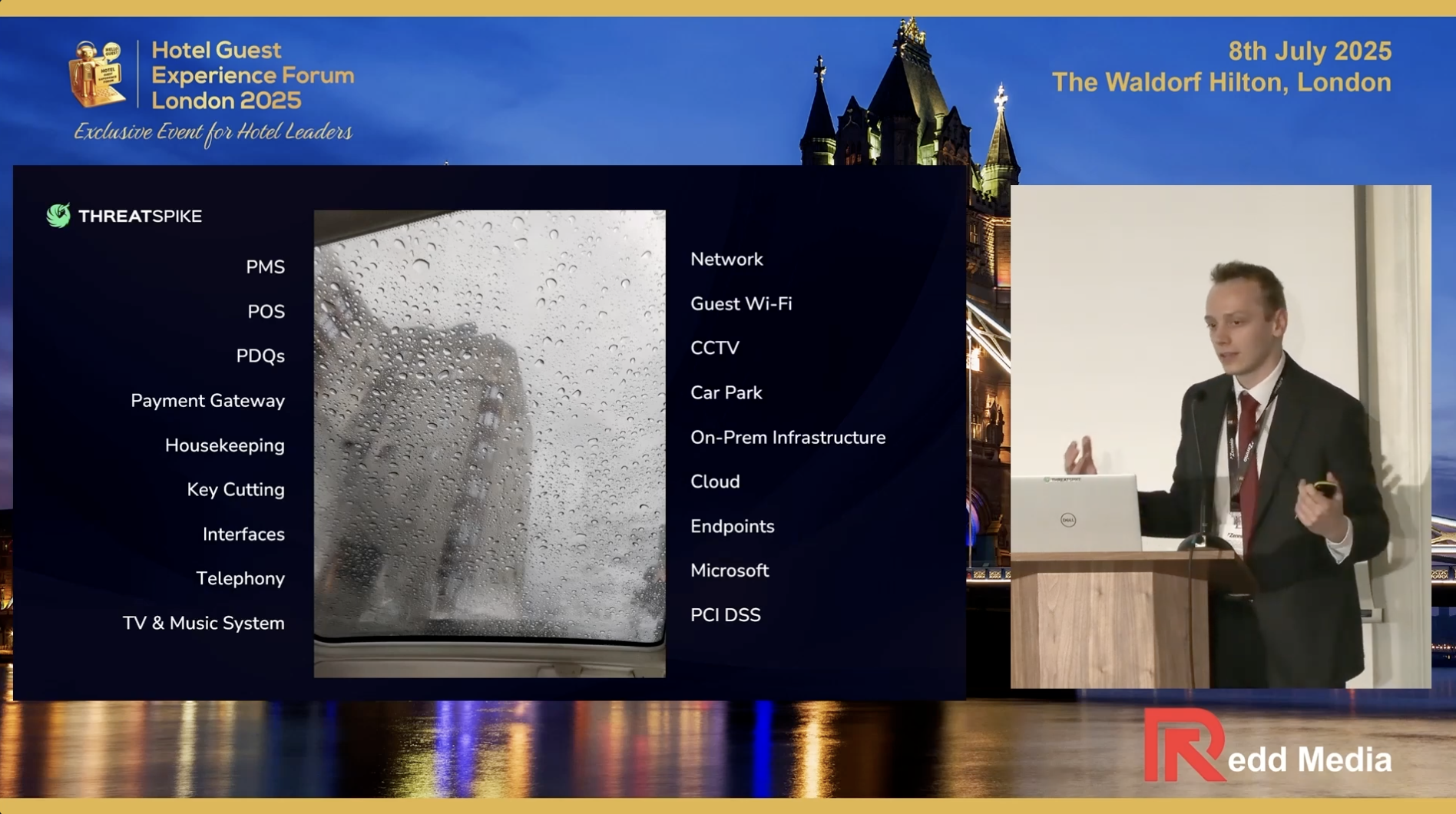
At ThreatSpike, we believe both the managed IT services and cybersecurity industries are overdue for change. Our blog is where we unpack what’s broken, share what we’ve rebuilt, and explore what’s next. Whether you’re a security leader navigating compliance burdens, a fast-scaling tech company overwhelmed by tools, or simply curious about the future of cyber defence, this is your place to stay informed.
Every post brings you closer to understanding the challenges we solve, the innovations we build, and the values that shape our approach. Welcome to the ThreatSpike Blog — your window into the minds of the people fixing IT.