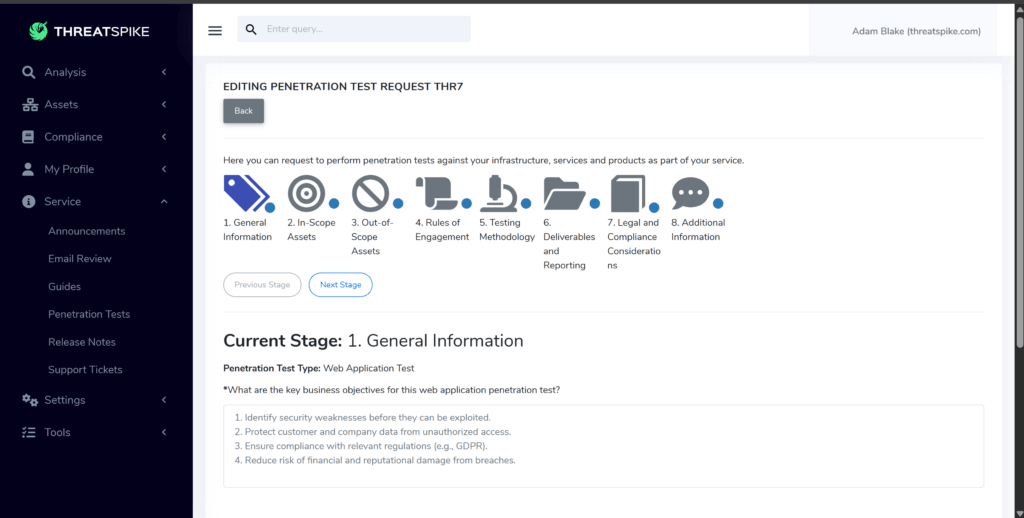
[New] Request a Pen Test from within the ThreatSpike Portal
You can now easily request a pen test from within the ThreatSpike Portal, following a simple guided questionnaire custom to each pen test type. Whether it’s a Red Team, Web App, or even a Physical – you can request it here!
[New] ServiceNow SaaS Integration
ThreatSpike now supports ServiceNow as a first-class Service Desk integration, with full bi-directional sync of comments and state (e.g., opened, reopened, closed) – including actions like sandboxing devices.
This further expands our suite of Service Desk Support integrations, ensuring you have a single-pane of glass for your security – regardless of how you’d like to be notified about incidents: ServiceNow, TOPDesk, Halo ISTM, the ThreatSpike Portal, or just via email.
[New] GCP Integration now identifies Suspicious Logins
ThreatSpike now raises incidents for suspicious logins on Google Cloud Platform. Whether it’s an unusual IP, risky geographical location, or weird User Agent – ThreatSpike has you covered.
And with our dedicated 24/7 SOC team on-hand to respond at all hours, you don’t have to worry – we’ll take care of it.
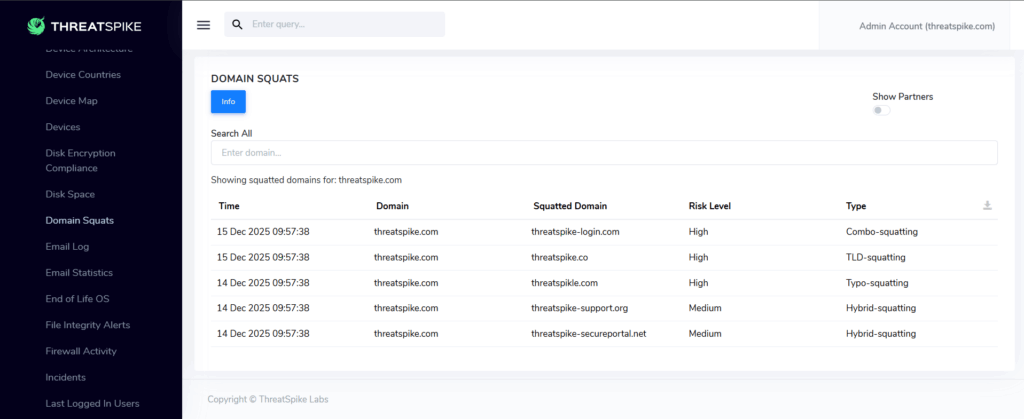
[New] Domain Squatting Identification
In our webinar last month, we talked about how phishing remains the most common way attackers gain access to your systems (for our in-depth analysis, watch the full recording.)
To help guard against this evolving threat, we are rolling out a new system to identify newly-registered suspicious domains. Using the latest research, we combine traditional heuristics with AI semantic analysis – resulting in state-of-the-art (2.5x existing) performance.
[New] Portal Authentication Improvements
MFA is now enforced for all users, ensuring that accounts are safe. This defaults to Email MFA – a new option! Users are sent an 8-digit MFA code to their registered email, valid for 5 minutes.
[New] Improved Microsoft Patching Reporting & Compliance
Microsoft has still not fixed various data quality issues with the Security Updates API they provide, despite some of them being reported almost 6 years ago.
We correct and work around affected patches as soon as possible, but recently the frequency of errors has increased significantly – beyond those previously identified – with Microsoft taking weeks to silently fix just a small percentage of the incorrect data.
This is not helped by frequent outages and poor performance of the Microsoft Update Catalog, which we can only assume is running on a laptop hidden somewhere in one of their cupboards.
In light of this, we have significantly streamlined our process to correct these errors inside the ThreatSpike platform – reducing the time for full deployment and propagation to all accounts from ~1 day to just half an hour.
Thank you to our customers who diligently report these errors. We appreciate your understanding while we work hard in the background to make sure the compliance information we report is as accurate as possible.
[New] Agent Performance Improvements (Network Analysis)
Up to 10x reduction in CPU usage with Network Analysis enabled. Domain Controllers benefit the most, but all devices (depending on network activity) will see some improvement. This will soon be rolled out to all devices (requires Agent Update).
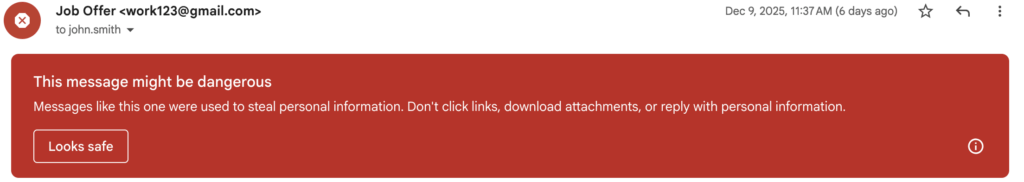
[New] Email Gateway: Per-mailbox ‘Monitor-only’ mode
We can now bypass the email gateway for individual users on request. This was previously an organisation-wide setting. These users will receive all email – even if it would otherwise be caught as spam/phishing – so we add threat classification headers to flag certain emails that we deem suspicious.
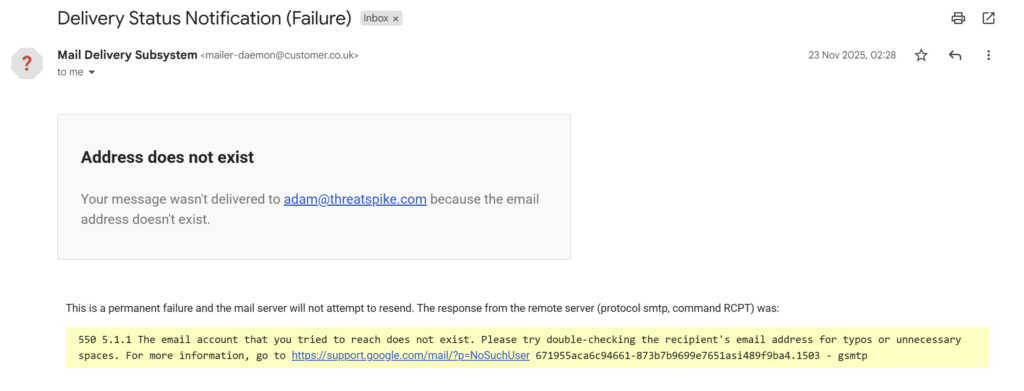
[New] Email Gateway: Non-Delivery Reports (NDRs)
Users now receive an email notification from us if their outgoing emails fail to send for 36 hours, with detailed diagnostic and error information to help us diagnose any outgoing email issues. Replies to the email notification are sent straight to the ThreatSpike Support team, who will be on hand to help identify and fix any issues.
[New] Email Gateway Performance & Reliability Improvements
Thank you to all of our users that diligently report spam and phishing emails that they receive – we are continuously working to improve our heuristics, and your feedback helps us improve the Email Gateway for all of our users. This is a constant game of cat and mouse, so we won’t go into details, but these improvements represent hundreds of hours of development work!
We’ve also increased our security protocol compatibility, fixing mail deliverability issues for outdated senders that were unable to verify their connection.
Additional Customer Requests
Many of the above new features and fixes came directly from customer requests. Other, smaller improvements we’ve made include:
- Allow customising the Firewall block page shown to users, just like you can do with the Web Filter and Phishing block pages. You can do this under “Settings -> Notifications”.
- Device Productivity and Browser Passwords can now be hidden, using the Privacy Shield (Settings -> Data Privacy).
- Users wanted more feedback when clicking “Run AV Scan” on the Device Overview page, as this previously silently failed if e.g., Windows Defender was disabled. We now warn if this is the case, and record the last start/end times when the AV scan completes.
- Added a password generator to the Credential Manager.
- We now use a monospace font when displaying passwords and license keys. No more getting confused between uppercase i and lowercase L when typing these in by hand!
- Sentinel One discovery now works as expected. Previously we may have reported machines with only Sentinel One running (and Windows Defender disabled) as non-compliant with AV.
- Improvements to some incidents raised by the Graph Security API integration. These should now display full evidence information. Some previously missing alerts should also now be raised correctly.
Thank you to everyone that provides feedback, particularly those who test out our new features. Where possible, we will always try to address your feedback, ensuring we are working with you to make ThreatSpike as useful and easy-to-use as possible.





