Humans are the weakest link in cybersecurity, and it is inaccurate to say that IT administrators, who often have access to sensitive data and systems, are invulnerable. In this blog post, we demonstrate how a Red Team Operator achieved full Active Directory domain compromise as a result of an IT Administrators’ poor cyber hygiene.
During red team engagements, when an operator manages to gain initial access into the Active Directory environment, the next course of action is to perform reconnaissance, move laterally and find avenues to escalate their privileges with the goal of achieving domain dominance. This is an iterative process, somewhat similar to the OODA loop, where the operator has to orient themselves in the environment, find out what privileges and access they have with the current compromised user/device and act upon the information to move to another device or obtain a new set of credentials. Orange Cyberdefense has a good mind map (OCD-mindmap) that provides extensive coverage of the techniques (and the relevant tools) that can be used depending on the situation a red team operator finds themselves in. After any success, such as obtaining a new set of credentials or access to a new device, the process repeats where the operator re-evaluates the situation and continues on the cycle until they have achieved the ultimate goal of obtaining Domain Administrator privileges.
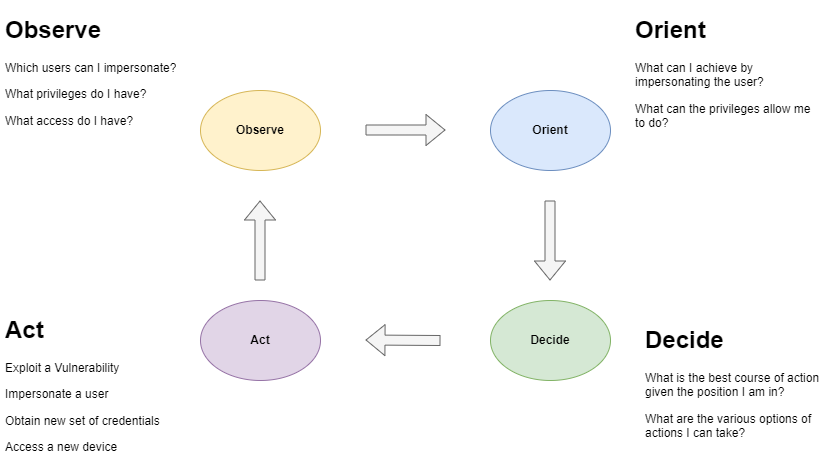
Figure 1: OODA Loop for Active Directory Testing
Starting Point
Our compromised host (say, HOST-PC-A) that allowed us to gain initial access was obtained through phishing, where the target user (say, DOM\JDOE) executed the C2 payload. Browser stored credentials were harvested from the compromised host and it was found that one of the stored passwords was also the domain password of the user. Next, we used Bloodhound ingestor to enumerate the Active Directory via LDAP queries to the Domain Controller. Bloodhound is a very useful Active Directory discovery tool that provides visualisation of the object relationships and various permissions between those relationships.
Finding Our Way
Using Bloodhound data, we were able to map the Active Directory environment and perform queries to help us understand the relationships between the objects in the Active Directory. Specifically, the objective here was to find out how we can escalate privileges with the current compromised user account. Using the built-in query of “Shortest Path to Domain Admins from Owned Principal”, there were no results returned – no easy win, as expected
However, the user JDOE was found to be part of the domain group “SVC-A Users” which had delegated Local Administrator privileges on 3 of the servers running SVC-A (SVC-A-SERVER1, SVC-A-SERVER2 and SVC-A-SERVER3).
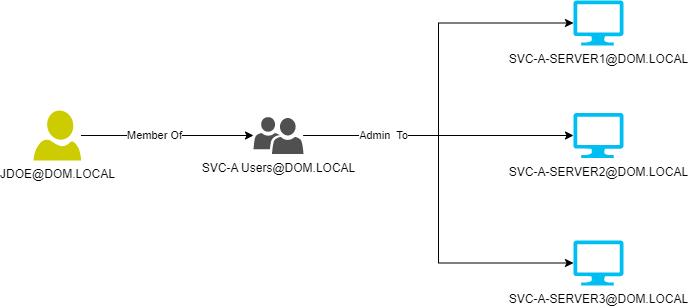
Figure 2: JDOE delegated Local Administrator rights
Using this information, naturally, the next course of action was to abuse the Local Administrator privileges to try and dump credentials from these servers. Using tools such as secretsdump from Impacket, we were able to dump the SAM hashes and LSA secrets from the SVC-A servers.
Moving Laterally as Local Administrator
Inspecting the credential dumps from the 3 servers, we were not able to find any credentials of domain users that were useful for lateral movement, as these were all users with the same privilege and access as JDOE. However, on a closer look, we noticed that the Local Administrator account ‘Administrator’ has the same hash across the 3 servers. This leads to the hypothesis that the Administrator account credentials are being reused. This is a common lapse of cyber hygiene in enterprise environments where IT administrators reuse the same password for the Local Administrator accounts out of convenience for device management.
To test our hypothesis, we used crackmapexec to perform a pass-the-hash attack, spraying the password hash of the administrator account for SVC-A-SERVER to a list of other servers in the domain. At this stage, we were able to access multiple servers in the domain as Local Administrator.
Privilege Escalation with Credentials from Idle Logon Sessions
Although we were able to authenticate as Local Administrator to multiple servers in the domain, unfortunately, the Domain Controllers were not using the same Local Administrator credentials. In order to escalate our privileges, we leveraged another common bad practice that IT Administrators often follow, which is to have idle active logon sessions on devices. Domain credentials of users with active sessions are stored in LSASS process memory and with Local Administrator privileges, we can dump the process memory and get our hands on these credentials. Our objective, by escalating privileges, is to get our hands on credentials of Domain Administrators so that we can authenticate to a Domain Controller. So, if we can find a Domain Admin user who has an active logon session on one of the servers we have Local Administrator privileges of, we will be able to obtain their credentials and impersonate them.
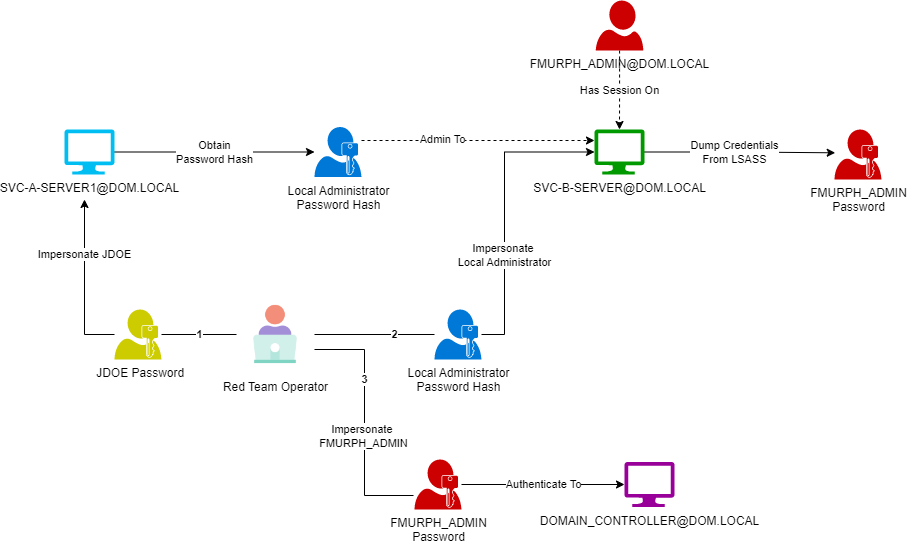
Figure 3: Attack Flow
To achieve this, we first obtained the list of Domain Administrators accounts, and for each of the user accounts, we enumerated the Servers where the user had active logon sessions. We managed to find a Domain Administrator account (DOM\FMURPH_ADMIN) having an active logon session on SVC-B-SERVER, on which we can authenticate using the previously obtained Local Administrator password hash. We then used lsassy to dump the LSASS memory on SVC-B-SERVER and obtain the password hash and clear-text password (legacy Windows server version) for DOM\FMURPH_ADMIN. With the password hash of FMURPH_ADMIN, we were able to perform a pass-the-hash attack to authenticate with the Domain Controllers as Domain Administrator and obtain full control of the domain.
Conclusion
In all, we capitalised on the poor cyber hygiene of IT administrators to help us with lateral movement and eventually escalated our privileges to Domain Administrator. The reuse of local administrator account passwords for devices allowed the Red Team operators to traverse across various devices in the domain easily with escalated privileges. With Domain Administrators having idle sessions on servers, the operators were able to use the previously obtained local administrator password hash to access these servers and dump the credentials of the Domain Admin user from LSASS memory. With the domain administrator’s credentials, we were able to impersonate the high-privileged user and have full control over the domain.
From this engagement we learn that sloppiness with cyber hygiene can result in devastating impact, especially if the user has privileged access. While attacks leveraging protocol weakness and misconfigurations are usually favoured for their high success rates, password reuse and cached credentials are still very relevant and should be on the go-to list of tests that a red team operator conducts.