Phishing continues to be the most common way attackers gain initial access. If you want to prevent phishing in your organisation, it starts with understanding how these campaigns suceed and why they continue to bypass traditional controls. Drawing on insights from our recent webinar Red Team Insights: What We’ve Learned from Breaching the Best, this article explores the tactics attackers rely on and the steps security teams can take to strengthen their defences.
You can watch the full recording for deeper examples and live demonstrations.
Why Phishing Works and How to Prevent It
Phishing remains the easiest route into a network. Modern campaigns use believable narratives, convincing impersonation and AI-generated language that mimics internal communication. This rise in quality makes it harder for users to spot malicious emails and easier for attackers to harvest valid credentials.
To prevent phishing, organisations need strong email security at the edge. Gateways should cover every domain, including parked or legacy ones that attackers still probe. Rules, threat feeds and blocklists must be updated frequently; ideally managed by a security team who can tune detections based on live attack activity. User awareness matters too; short, regular training keeps staff alert without overwhelming them.
If you missed the live session, the recording includes real phishing scenarios used against high-security environments.
Securing Remote Access Before It’s Exploited
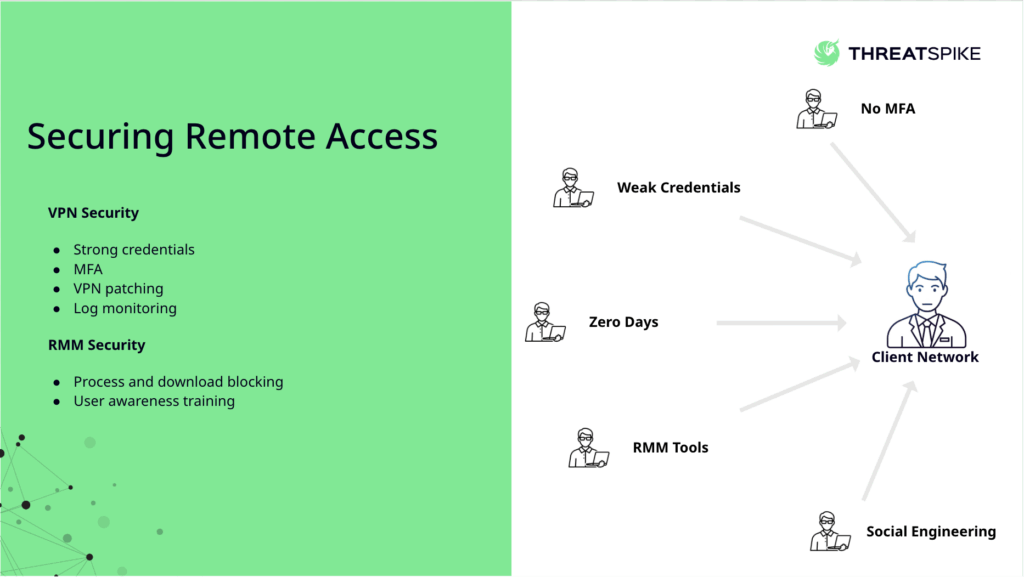
Once credentials are stolen, attackers move straight to VPNs or RDP portals. A single reused password can turn a phishing click into a full network compromise. This link between phishing and remote access weaknesses is a key theme covered in the webinar.
Strong credentials and MFA are essential. VPNs, firewalls and remote access tools must be patched quickly, as unpatched appliances remain one of the most common footholds we see. Continuous monitoring for unusual logins or odd session behaviour helps detect intrusions early.
Protecting High-Privilege Accounts
Domain admins and cloud tenant admins remain prime targets. Once attackers reach these accounts, they can deploy ransomware or disable logging before moving laterally.
During the webinar, our red team walked through examples of privilege escalation chains that began with a simple phishing email.
Prevention begins with strict password policies, secure storage and regular audits of who genuinely needs privileged access. Least privilege should be enforced consistently, and any change to admin groups should trigger an immediate review. Centralised monitoring for privilege escalation attempts helps spot misuse or stolen credentials; this is where a service like ThreatSpike Blue proves its worth, giving you continuous visibility into privileged activity and real time investigation when something looks off.
Quick Checklist to Help Prevent Phishing Attacks
- Deploy and maintain secure email gateways across all domains
- Enforce MFA for every remote access point
- Patch VPNs and firewalls as quickly as possible
- Train staff to recognise modern phishing patterns
- Audit privileged accounts and enforce least privilege
- Monitor for unusual login behaviour and escalation attempts
FAQ: Preventing Phishing in 2026
What is the most effective way to prevent phishing in a business?
A combination of well-configured email security, MFA everywhere and continuous user training delivers the strongest results.
How do phishing attacks bypass security tools?
Attackers mimic internal communication, use trusted cloud services and exploit weak or outdated email gateway rules.
Which staff need the most training?
Anyone handling finance, HR or administrative tasks, as these roles are most frequently impersonated or targeted.
Final Thoughts
Red team operations show that preventing phishing is not about a single control; it’s about layered defences, ongoing monitoring and a culture of awareness. The organisations that fare best combine strong technology, disciplined processes and regular user education.
If you want a deeper look into how these attacks unfold in real environments, watch the full webinar recording. It covers real red team breaches, live demos and practical steps your organisation can take straight away.





