Why IT and Cybersecurity for Hospitality Matter More Than Ever
The hospitality sector is more digitally connected than ever. That progress brings increased risk. From booking engines and guest Wi-Fi to PMS platforms and payment systems, every part of a hotel’s operation now relies on a robust IT and cybersecurity backbone. But are most hotels truly prepared with an IT and Cybersecurity solution that covers every evenutality?
Live from The Waldorf – What We Learned from Hospitality IT Leaders
Earlier this year, the ThreatSpike team attended and sponsored a the Hotel Guest Experience Forum held at The Waldorf in London. Surrounded by industry leaders and innovators, we had the opportunity to hear firsthand about the operational pressures hoteliers face and share how we’re helping brands stay secure while scaling digital transformation.
Watch the Full Talk: A Practical Guide to IT and Cybersecurity for Hospitality
In this featured talk, Jacob Andrews, Head of ThreatSpike Black, shares practical insights from working with leading hotel groups to overhaul their IT and cybersecurity for hospitality. He explores the complexities of hospitality tech environments, where even small gaps in system management or security protocols can expose guest data or disrupt critical services.
What You’ll Learn in This Session
- Why hospitality IT often falls short and how to fix it
- What a modern managed service provider should actually deliver
- How ThreatSpike helped transform one hotel group’s IT operation from outdated support and patchy compliance to full 24/7 coverage, better tooling and PCI-readiness
Full Transcription
Strengthening IT and Cybersecurity in Hospitality
Today, I’ll be speaking about how we can strengthen IT and cybersecurity in hospitality in order to enable guest trust and support innovation.
Every day, your properties process thousands of transactions, store vast amounts of personal data and manage hundreds of devices. But the question is: how secure is the backbone that supports all of this?
The trend is clear. As the guest journey becomes increasingly digital, from booking to checkout—so does your exposure to cybersecurity vulnerabilities, data breaches and fraudulent activity.
So, what’s the plan? In theory, it’s simple. You invest in cybersecurity tooling, onboard new service providers, deploy more operational processes and manage risk more effectively. In practice, though, it’s a lot easier said than done.
Before going further, let me quickly introduce ThreatSpike. We’re a cybersecurity company that’s been operating for over 10 years. From the beginning, our focus has been on consolidating security tooling in a fragmented market, something we still do today. Our competitive pricing helped us win a significant number of customers early on, especially in the hospitality sector.
Some of the hospitality brands we work with include Capinky Hotels, Aman Resorts, PPHE, Invest Hotels, Maybourne, Imperial Hotels, Malmaison and Pyramid Global Hospitality. The list continues to grow.
As for me, I’m Jacob Andrews, Head of Black at ThreatSpike. “Black” is our managed IT service, which we launched last year. The idea came directly from conversations with our hospitality clients. We saw that many of the IT service providers they were using simply weren’t good enough.
Bridging the IT Gap
The MSP market is, in our view, largely reactive. Many providers just resell tools at market prices, treat support as an afterthought and fail to bridge the gap between IT and cybersecurity in hospitality. That’s where we saw an opportunity. Being a software company, we’re in a strong position to bridge that gap. We build all of our solutions in-house, every security and IT tool is developed and owned by ThreatSpike, allowing us to deliver a fully integrated service and product.
Hospitality is inherently complex. From a service and support perspective, it’s vital to take control where you can. Otherwise, things fall through the cracks and critical systems are left unmanaged. That’s why our offering is comprehensive, we aim to cover everything.
With ThreatSpike Black, you also get Ryan, who leads our Red Team (offensive security and penetration testing), and Chandler, who heads up Blue Team (defensive security tooling). Together, they cover the full cybersecurity spectrum.
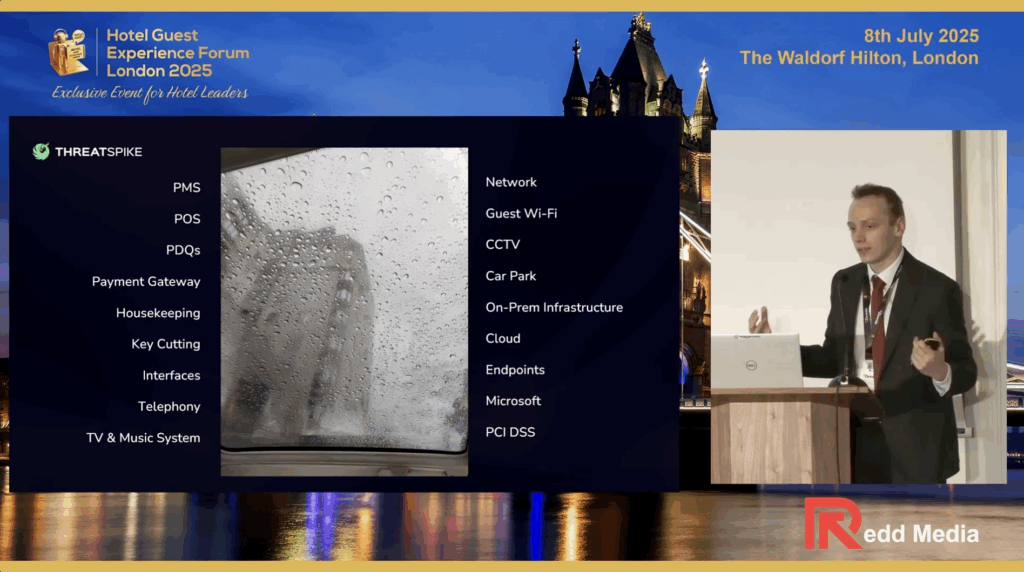
Let me give you a quick analogy. I was on my way to a client in London recently, sitting in a taxi after it had rained. Looking up through the sunroof, I noticed the raindrops on the glass and thought it was a fitting metaphor for hospitality. Each droplet represents a part of your operation: the PMS, PDQs, guest Wi-Fi, car parking systems, TV and music, key cutting, endpoints, infrastructure and all the interfaces connecting it all. It’s a lot to manage, and not enough credit is given to how complex it really is.
A Real-World Example
Let’s explore a case study from one of our hospitality clients with around 1,000 users and eight properties. When we first engaged, their existing MSP was providing only basic services, first-line support, user provisioning and password resets. Anything more complex was escalated to an internal team that was, in reality, still operating as first-line support.
Processes were weak. Security tooling was outdated and ill-suited to their needs. Offensive security was almost non-existent. Their PCI compliance score was low, and infrastructure issues were rampant.
After onboarding with ThreatSpike, we immediately improved their security posture. We implemented 24/7 SOC support, full incident response and endpoint protection. Within days, over 80 security controls were enabled across their environment.
Since all of our solutions are our own, we moved fast to consolidate and replace many of their third-party tools. We replaced their VPN, remote screen sharing, asset inventory, help desk and more with ThreatSpike tools. We created bespoke automations and carried out comprehensive testing, including red teaming and PCI audits.
When it came to support, we didn’t just manage the technology, we embedded ourselves in the business. Our team spent over five months on-site to learn their operations inside-out. We sat with front-office staff, housekeeping, maintenance, every department that contributes to guest experience.
We looked for issue fatigue and unaddressed problems, but also assessed how well their applications were understood and used. Changing hotel software is expensive and disruptive, so we took over application management and also assumed responsibility for infrastructure, cloud and third-party vendor management.
We freed up internal IT teams from daily user support tasks so they could focus on strategic projects, something that, in our view, is sorely lacking across the hospitality sector.
We often find that “roads have already been travelled” when we come in, meaning IT teams have attempted big projects without laying the proper infrastructure and security foundations. These shortcuts cause cracks that later need to be redone. Our job is to help you build those roads correctly the first time.
We also helped the client achieve full PCI compliance. PCI is a strong roadmap for becoming fully secure, but the challenge is not implementing it, it’s maintaining it over time. A single misconfiguration or missed patch can compromise months of effort. We help clients stay compliant on an ongoing basis.
Additionally, we supported them in working towards Cyber Essentials Plus, improving supply chain assurance and navigating cyber insurance processes. We helped establish IT policies and improved operational procedures.
Some of the other highlights include building a dedicated internal knowledge base. The hospitality workforce is fluid—people move frequently between properties and roles. By documenting knowledge in a centralised, wiki-style system, we created redundancy that safeguards against key-person risk.
We also helped with IT recruitment. Many clients who experience our service team firsthand ask us to recruit similar talent for their in-house roles, and we support them with that process as well.
Our Three-Stage Approach
We call this the ThreatSpike Transformation, which happens in three stages:
- Discovery: Understanding what exists and what’s missing in your IT and security landscape.
- Implementation: Developing a roadmap that includes both fixes and future projects—whether it’s improving backups or moving to new cloud infrastructure.
- Continuity: This is the hardest part—sustaining the changes and continuing to improve over time.
So, who is ThreatSpike? We are your IT and security partner.